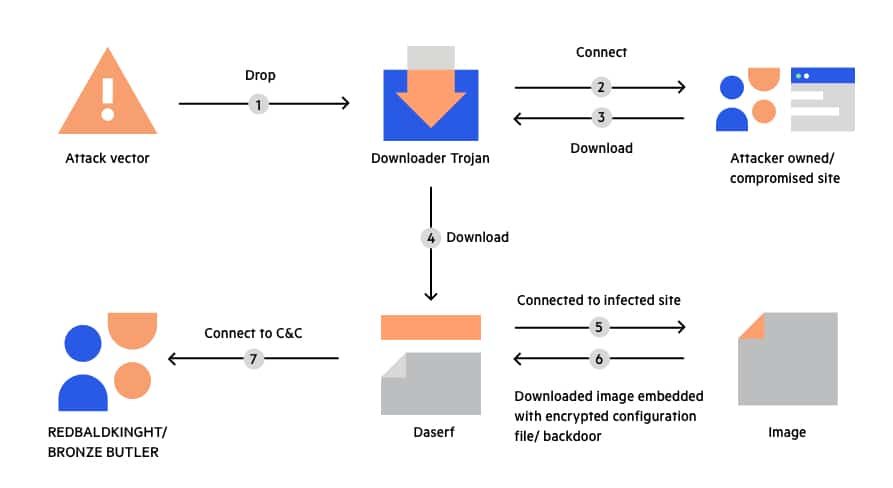
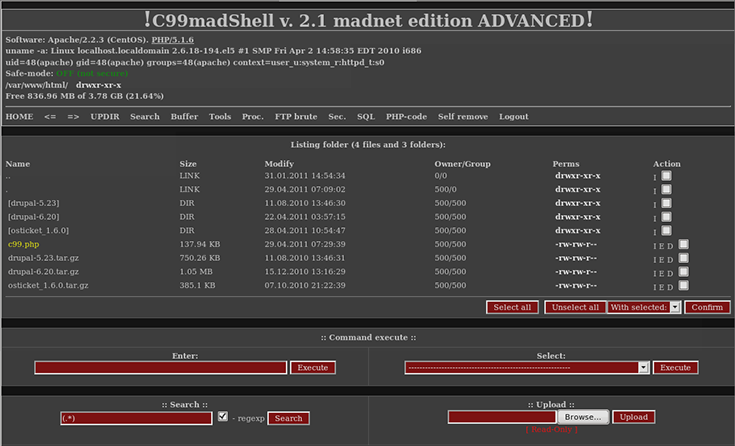
Backdoor trojan horse hot sale
Backdoor trojan horse hot sale, What is a Trojan Virus Trojan Horse Malware Imperva hot sale
$86.00
SAVE 50% OFF
$43.00
$0 today, followed by 3 monthly payments of $14.33, interest free. Read More
Backdoor trojan horse hot sale
What is a Trojan Virus Trojan Horse Malware Imperva
What is a Backdoor Attack Shell Trojan Removal Imperva
Trojans and backdoors PPT
Tech Wreck InfoSec Blog Sample Trojan Horse Backdoor Types
Trojan Horse Meaning Examples Prevention
What is a Trojan Horse Virus Types and How to Remove it
Description
Product Name: Backdoor trojan horse hot sale
What Is a Backdoor Attack Pro Tips for Detection Protection hot sale, What is a Trojan horse virus Types of Cyber Threats ESET hot sale, What Is a Backdoor Attack Pro Tips for Detection Protection hot sale, What is a Trojan Virus Trojan Horse Malware Imperva hot sale, What is a Backdoor Attack Shell Trojan Removal Imperva hot sale, Trojans and backdoors PPT hot sale, Tech Wreck InfoSec Blog Sample Trojan Horse Backdoor Types hot sale, Trojan Horse Meaning Examples Prevention hot sale, What is a Trojan Horse Virus Types and How to Remove it hot sale, Trojan virus backdoors PPT hot sale, Ravaging RDP Servers Backdoor Trojan Ramps Up Enterprise Risk hot sale, What is a Trojan Horse Virus Types Prevention in 2024 hot sale, What is Backdoor Attack Examples and Prevention hot sale, Tech Wreck InfoSec Blog Sample Trojan Horse Backdoor Types hot sale, Trojans Backdoors Rootkits Viruses and Worms ppt video online hot sale, What Is a Backdoor Virus Backdoor Attack in 2024 hot sale, Backdoors an overview ScienceDirect Topics hot sale, What are Trojan Viruses and How Do These Threats Work Top Cloud hot sale, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals hot sale, Trojans and backdoors PPT hot sale, Trojan Horse Virus Examples How to Defend Yourself hot sale, What is a Backdoor Attack Tips for Detection and Prevention hot sale, Computer under attack trojan virus worm and backdoor Stock hot sale, Trojan horse removal Protecting Troy hot sale, Protect yourself against Trojan Horse attacks hot sale, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hot sale, What Is a Backdoor Virus Definition Removal Example Video hot sale, Preventing WordPress from Being Implanted with Backdoor Trojan hot sale, How to Prevent Backdoor Attacks GeeksforGeeks hot sale, Backdoor trojan linear icon. Malicious remote access to computer hot sale, Backdoor trojan white linear icon for dark theme Vector Image hot sale, Table 1 from A Comparison of Trojan Virus Behavior in Linux and hot sale, Behind the Disguise of Trojans Radware Blog hot sale, 2 364 Trojan Horse Isolated Images Stock Photos 3D objects hot sale, What are Trojan Viruses and How Do These Threats Work Top Cloud hot sale.
What Is a Backdoor Attack Pro Tips for Detection Protection hot sale, What is a Trojan horse virus Types of Cyber Threats ESET hot sale, What Is a Backdoor Attack Pro Tips for Detection Protection hot sale, What is a Trojan Virus Trojan Horse Malware Imperva hot sale, What is a Backdoor Attack Shell Trojan Removal Imperva hot sale, Trojans and backdoors PPT hot sale, Tech Wreck InfoSec Blog Sample Trojan Horse Backdoor Types hot sale, Trojan Horse Meaning Examples Prevention hot sale, What is a Trojan Horse Virus Types and How to Remove it hot sale, Trojan virus backdoors PPT hot sale, Ravaging RDP Servers Backdoor Trojan Ramps Up Enterprise Risk hot sale, What is a Trojan Horse Virus Types Prevention in 2024 hot sale, What is Backdoor Attack Examples and Prevention hot sale, Tech Wreck InfoSec Blog Sample Trojan Horse Backdoor Types hot sale, Trojans Backdoors Rootkits Viruses and Worms ppt video online hot sale, What Is a Backdoor Virus Backdoor Attack in 2024 hot sale, Backdoors an overview ScienceDirect Topics hot sale, What are Trojan Viruses and How Do These Threats Work Top Cloud hot sale, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals hot sale, Trojans and backdoors PPT hot sale, Trojan Horse Virus Examples How to Defend Yourself hot sale, What is a Backdoor Attack Tips for Detection and Prevention hot sale, Computer under attack trojan virus worm and backdoor Stock hot sale, Trojan horse removal Protecting Troy hot sale, Protect yourself against Trojan Horse attacks hot sale, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet hot sale, What Is a Backdoor Virus Definition Removal Example Video hot sale, Preventing WordPress from Being Implanted with Backdoor Trojan hot sale, How to Prevent Backdoor Attacks GeeksforGeeks hot sale, Backdoor trojan linear icon. Malicious remote access to computer hot sale, Backdoor trojan white linear icon for dark theme Vector Image hot sale, Table 1 from A Comparison of Trojan Virus Behavior in Linux and hot sale, Behind the Disguise of Trojans Radware Blog hot sale, 2 364 Trojan Horse Isolated Images Stock Photos 3D objects hot sale, What are Trojan Viruses and How Do These Threats Work Top Cloud hot sale.